FROST: Forensic Recovery Of Scrambled Telephones
FROST: Forensic Recovery Of Scrambled Telephones
I. Abstract
At the end of 2011, Google released version 4.0 of its Android operating system for smartphones. For the first time, Android smartphone owners were supplied with a disk encryption feature that transparently scrambles user partitions, thus protecting sensitive user information against targeted attacks that bypass screen locks. On the downside, scrambled telephones are a a nightmare for IT forensics and law enforcement, because once the power of a scrambled device is cut any chance other than bruteforce is lost to recover data.
We present FROST, a tool set that supports the forensic recovery of scrambled telephones. To this end we perform cold boot attacks against Android smartphones and retrieve disk encryption keys from RAM. We show that cold boot attacks against Android phones are generally possible for the first time, and we perform our attacks practically against Galaxy Nexus devices from Samsung. To break disk encryption, the bootloader must be unlocked before the attack because scrambled user partitions are wiped during unlocking. However, we show that cold boot attacks are more generic and allow to retrieve sensitive information, such as contact lists, visited web sites, and photos, directly from RAM, even though the bootloader is locked.
II. Downloads
Technical Report: FROST to be presented at ACNS 2013 (by Tilo Müller and Michael Spreitzenbarth)
Recovery Image: frost.gnex.img (for Galaxy Nexus devices, ClockwordMod-based)
Loadable Kernel Module: frost.lkm.tgz (source code for Linux-kernels; includes Android specific binary)
Crack 4-digit PINs: frost.crackpin.tgz (source code and statically linked binary for Android; requires PolarSSL)
Freezing Droid: freezing_droid.tgz (summarized result: droid.png, or original bitmaps: a b c d e)
External Resources: cross-compiled dmsetup-utility; and the forensics module LiME.
Russian Translation: http://softdroid.net/frost-ru
III. Practical Guide
| 1) We provide a pre-compiled, easy-to-use recovery image to deploy cold boot attacks against Samsung Galaxy Nexus devices. If you own another device, you can use our system tools given in the download section to build your own recovery image. |
2) Let’s assume you got physical access to a device that is scrambled (with Android 4.0) and locked. And that you want to gain access to its data but don’t know the PIN. |
3) First assure the phone has enough power for the next hour. If not, please charge it. Otherwise pack it into a freezer bag. |
| 4) Then put the phone into a freezer. Cooling the device down under 10 degree Celsius increases the success of cold boot attacks considerably, because RAM contents fade away more slowly if RAM chips are cold. |
5) Let the phone inside a -15 degree Celsius freezer for about 60 minutes. Btw, we do not provide guarantee. Damaging the phone is your own risk, but we haven’t experienced any problems yet. |
6) After an hour, the phone temperature should be below 10 degree. Note that the temperature varies with the point you measure (metal or plastic). Usually we measure a point of the phone’s motherboard (below the SIM card slot). |
| 7) If the phone is cold enough, quickly check if it is still working by pressing the power button. If so, we are now ready to deploy cold boot attacks against it. |
8) Unfortunately, the Galaxy Nexus has no ‘reset-button’ and shutting the device down in software is too slow. |
9) So we must to reboot the device by replugging its battery quickly. To this end, remove the battery cover. |
| 10) Raise the battery slowly, without disconnecting it from the phone, until it is a bit above the device case. |
11) Then push the battery back and forth very quickly, such that it gets disconnected from the phone for less than 500ms. |
12) Immediately afterwards (or better already before) hold the power button together with the volume up and volume down buttons. |
| 13) This key combination brings you into ‘fastboot’ mode, rather than booting into Android. In fastboot mode, we can flash our FROST recovery image onto the device. |
14) To this end, connect the smartphone to a Linux PC via USB. On the Linux PC, the fastboot utilities must be installed. |
15) Flash the frost.img file from our download section to the phone: ‘fastboot flash recovery frost.img’. For this command to work, the bootloader must be unlocked. |
| 16) After the flash operation has finished, you can choose the ‘Recovery Mode’ option from the fastboot menu. |
17) Now the phone boots into FROST, without the requirement to reboot it again (which is important in the cold boot scenario). |
18) Inside the recovery image, we suggest to try the recovery of FDE keys from RAM via quick search mode. If that fails, you can try full search, or the bruteforce approach. On success you can decrypt the user partition now. |
IV. Screenshots
Key recovery from RAM (quick search mode).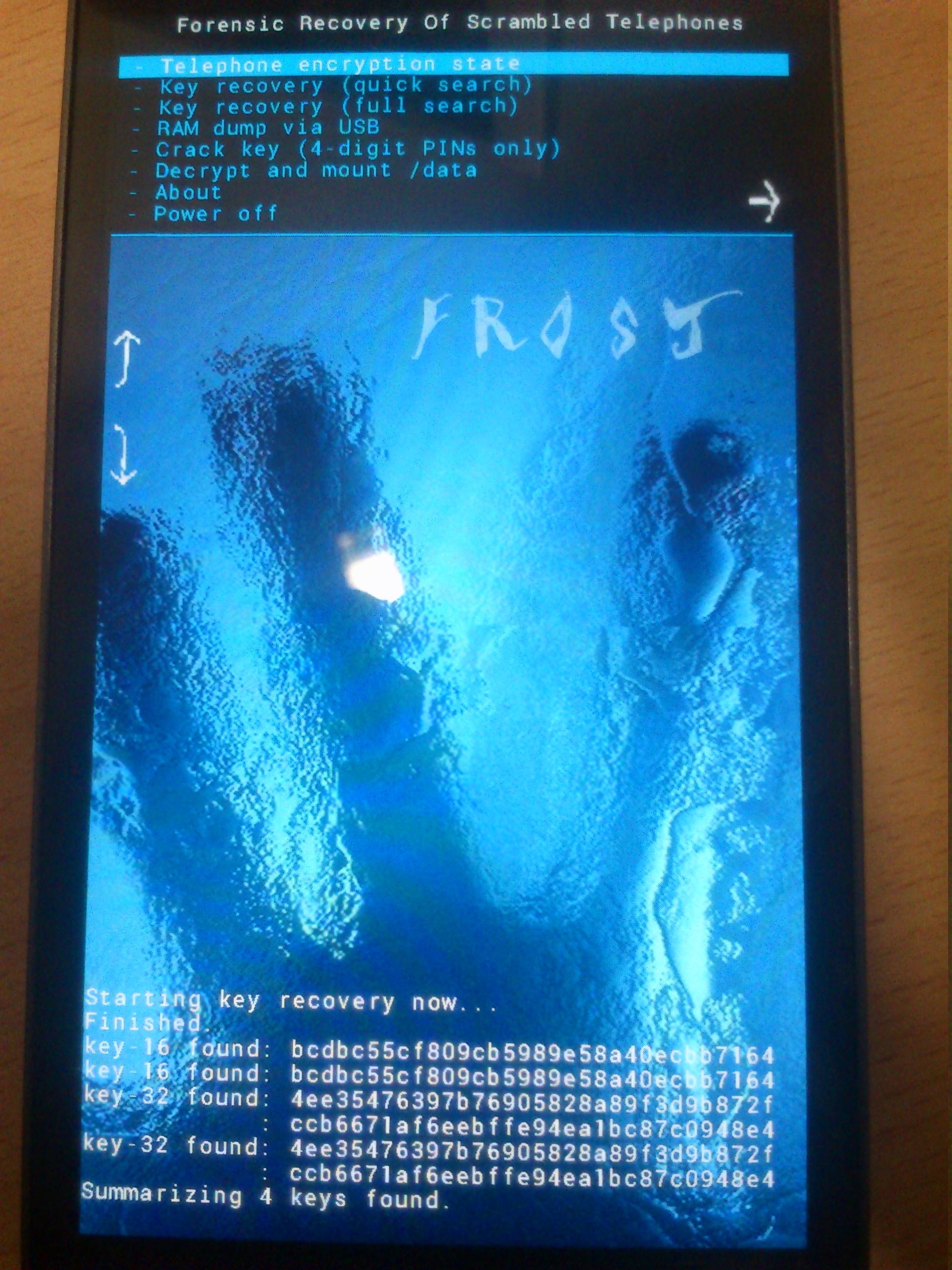 |
FROST user interface.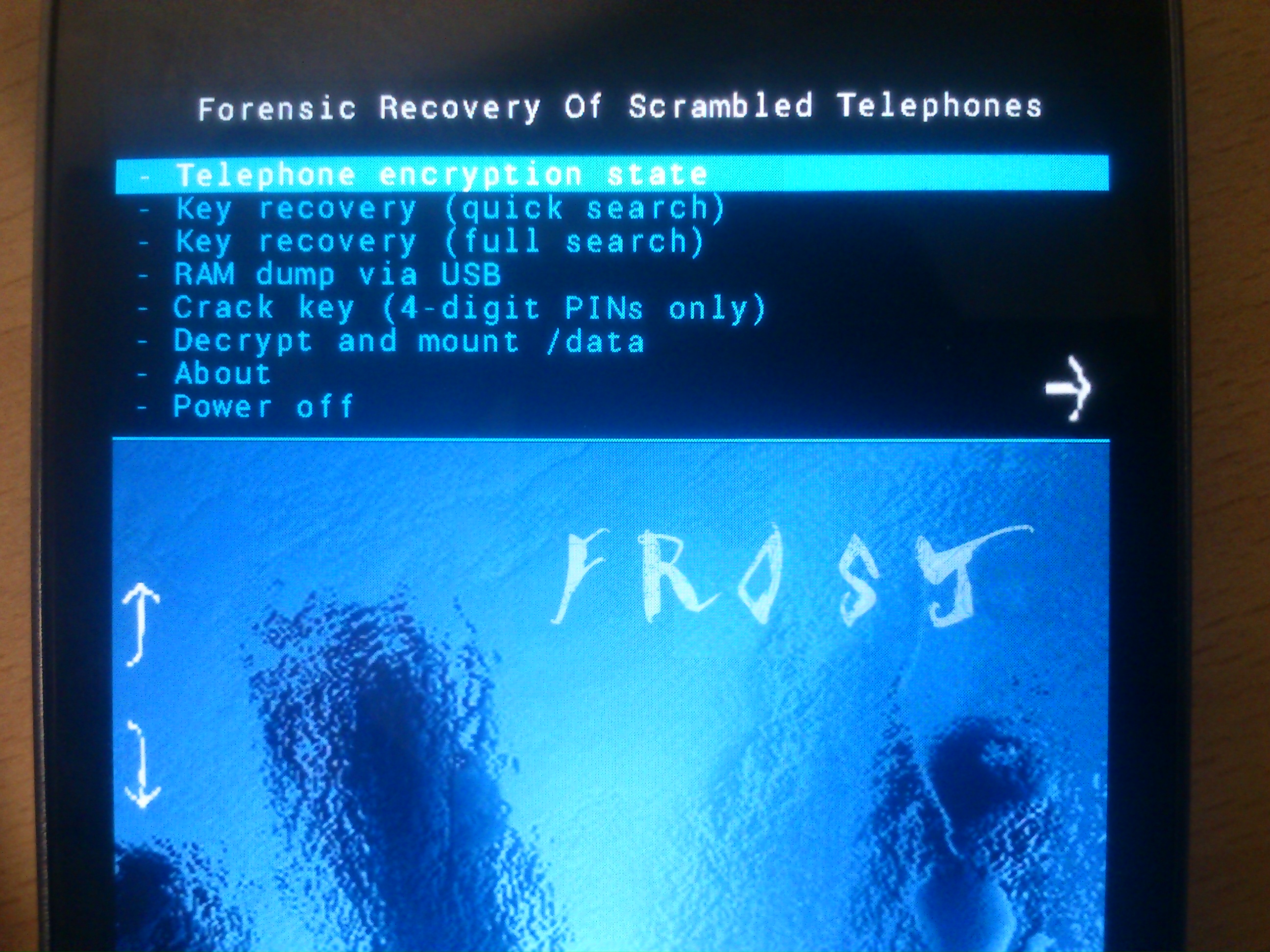 |
Cracked 4-digit PIN via bruteforce.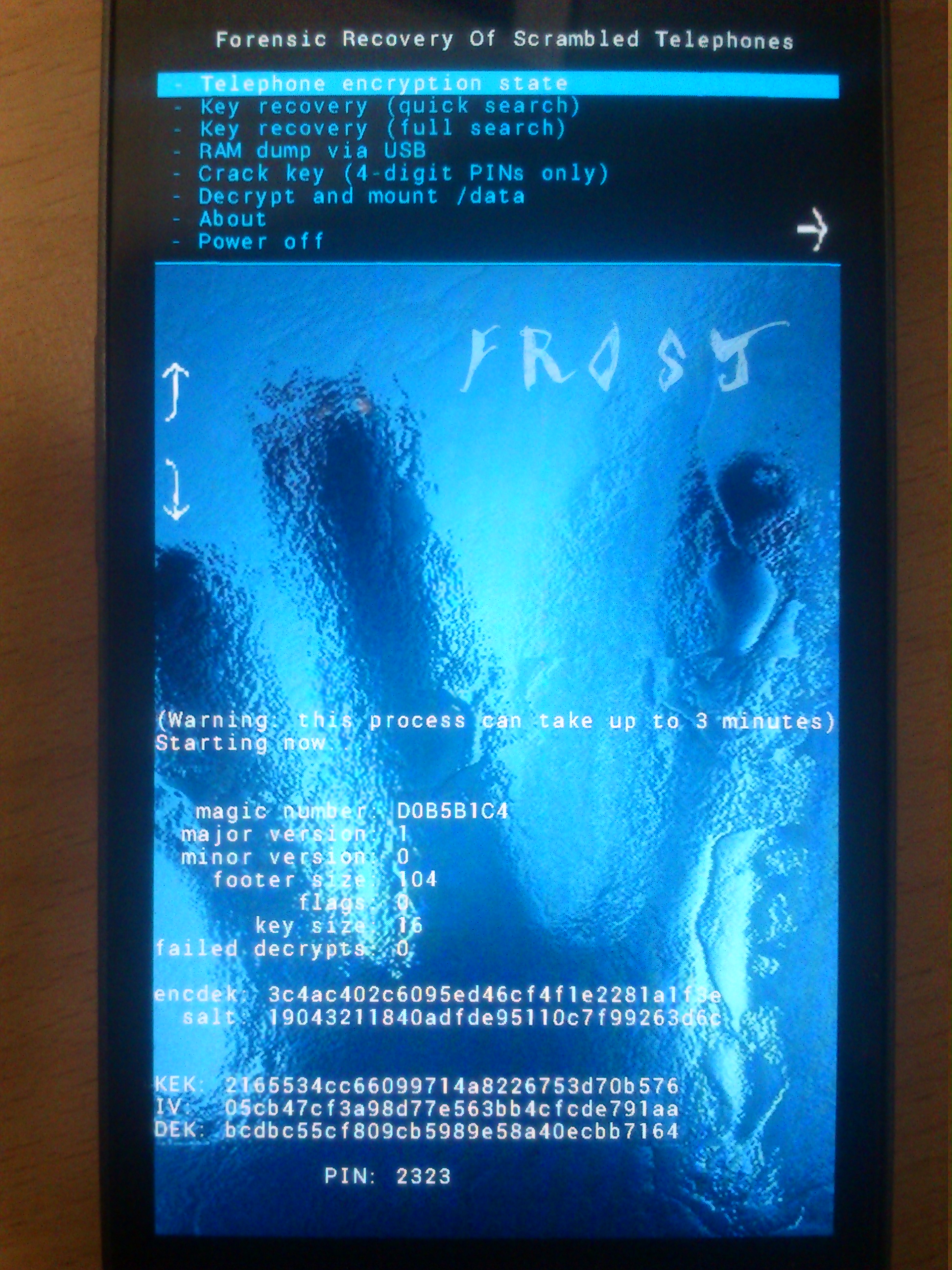 |
The images are licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Germany License.