ContrOWL: A new security app based on crowed intelligence

ContrOWL: A new security app based on crowed intelligence
ContrOWL is a security app that helps you find potential threads among your installed apps. It can also check freshly added apps on the fly and notify you if an app is rated as suspicious. ContrOWL also gives you information about top used permissions and broadcast intents of malware apps which should help you to evaluate them. Please read the help tab in ContrOWL to better understand how to use and understand it. The rating that tells whether an app is a potential thread or not is based on a study which evaluated about 16.000 malware apps and 100.000 goodware apps. The rating is purely based on permissions and broadcast intents fetched by the apps and for that not always correct. So maybe you will have non-malware apps with a high rating (high is bad and 100 is worst) that actually do no harm. Practice has shown that false positives can have two reasons:
- First the app has only few permissions or broadcast intents and for that the calculation is not as accurate as for apps with many permissions and broadcast intents.
- Second the app uses permissions and broadcast intents that could do harm and are often used by malware apps.
Anyway it is recommended to check apps with a high rating and therefore ContrOWL offers details about the permissions and broadcast intents and how other users evaluated this app. Of course each user can evaluate apps as malware, goodware or “not sure” at any time in the details section or after removal of an app. Your votes don’t show up immediately in the total votes part because for security reasons all votes will be buffered, checked and later inserted in the main database. Your personal votes are displayed in the application list and the application details.
Please take part in the voting system because crowd intelligence is a great way to determine false positives and negatives. Also inform the author via the help-tab in ContrOWL about Bugs, suggestions for improvements or other issues.
Important:
ContrOWL does not give a guarantee whether an app is malicious or not and therefore I will not be liable for damage caused by misinterpretations made by ConrOWL.
Known issues and planed features for next versions:
- Better support for softkey only devices (Devices without a menu button can’t sort the lists)
- To fulfill the support for softkeys switch from tab layout to action bar layout
- Sorting possibilities in permissions, intents and apps details
- repair button (If frequent reports about bugs I can’t fix come in)
- Better layout for tablets (currently I could only test it on a tablet emulator and it worked but didn’t look very nice)
Screenshots:
Help and information tab inside the app.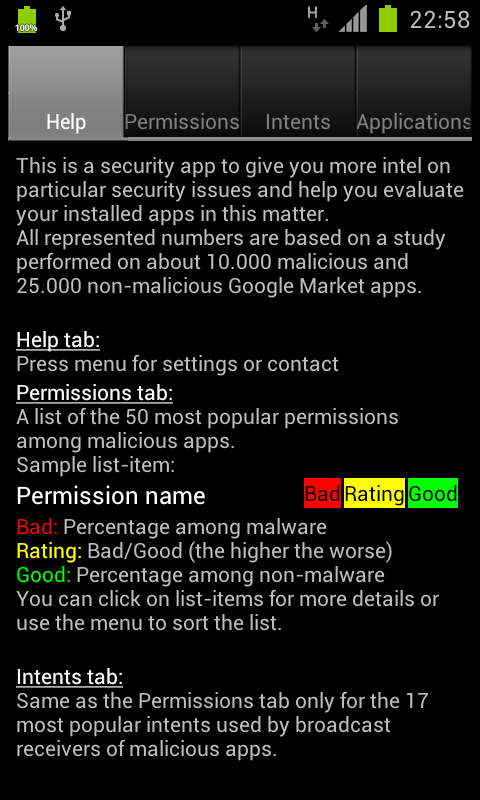 |
Permissions rating overview.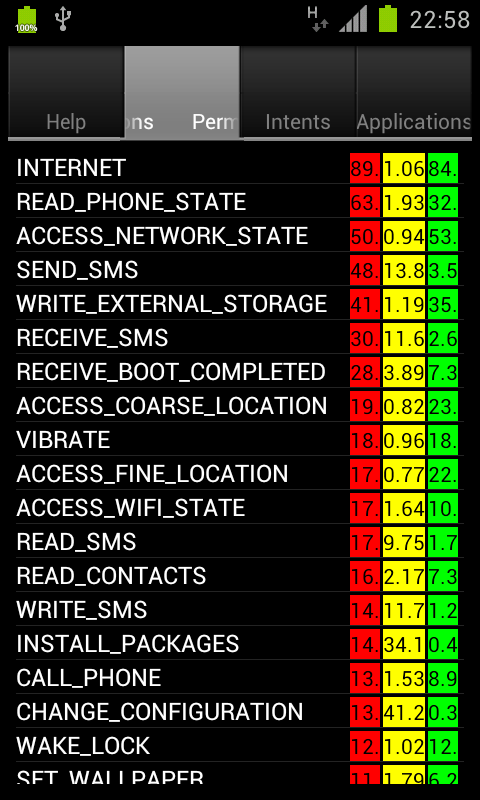 |
Intents rating overview.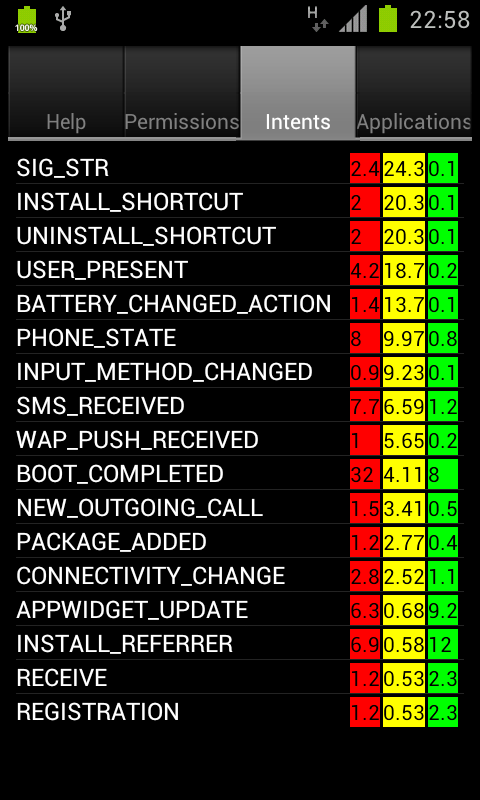 |
Detailed app rating.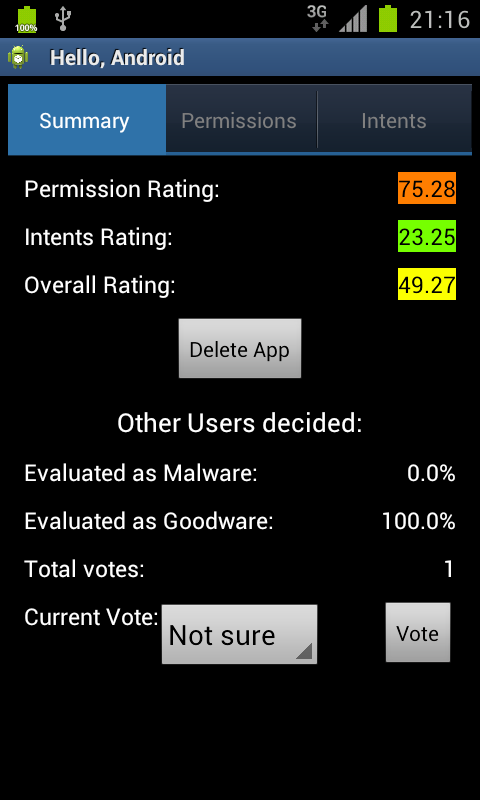 |
Information and Contact:
Bachelor thesis by Marcel Hrnecek
Project advisor: Michael Spreitzenbarth
