PyBox – A Python Sandbox
The application of dynamic malware analysis in order to automate the monitoring of malware behavior has become increasingly important. For this purpose, so-called sandboxes are used which provide the functionality to execute malware in a secure, controlled environment and observe its activities during runtime. While a variety of sandbox software, such as the GFI Sandbox (formerly CWSandbox) or the Joe Sandbox, is available, all solutions are closed-source. We have developed PyBox, an open-source sandbox written in Python. PyBox can be used to build customized sandbox solutions for malware research.
PyBox Design
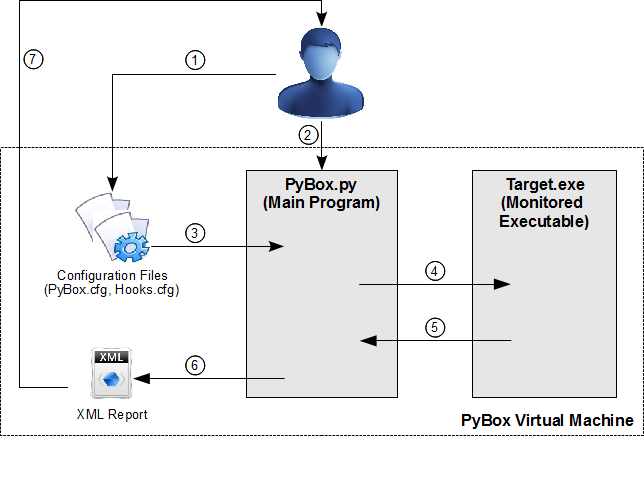
The PyBox analysis environment consists of three major parts: a virtual machine, the analysis tool PyBox.py, and the hook library pbMonitor.dll. The following picture gives an overview of the system and we explain the components in more detail below (click on the image to enlarge).
Virtual Machine
Using a virtual machine as a basis for malware analysis guarantees a secure and controlled environment in which the malware can be executed and the original system state can be restored afterwards. Inside the virtual machine we observe system activity of a certain software through monitoring the calls to the native Windows API by using inline API hooking in combination with DLL injection.
Analysis Tool
The analysis tool, called PyBox.py, acts as the hook server. The hook server is responsible for setup adjustments according to the settings defined in the configuration files, target process creation, and hook library injection. During the execution of malicious software, it also receives and processes the log data from the hooked API functions and in the end generates a final report.
Hook Library
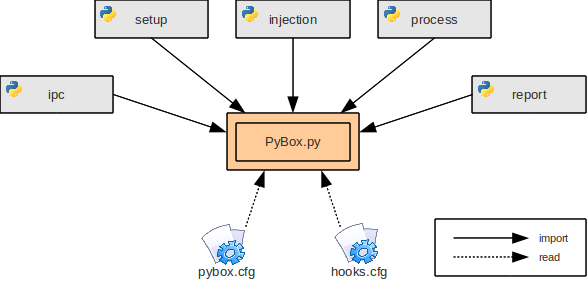
The hook library pbMonitor.dll implements the actual hooking and monitoring functionality. It is responsible for installing the specified hooks, monitoring the system calls, and creating log entries which are then send to the hook server. Therefore, the hook library and the hook server have to interact with each other very closely by means of inter-process communication (IPC). This way communication and information exchange between the two processes is straightforward. A schematic overview of the different parts of PyBox and their interaction is displayed in the following figure (click on image to enlarge).
The hook library pbMonitor.dll is the only component implemented in Visual C++. In this case we have chosen C++ as programming language because Python cannot create DLL files and we have to make much use of various API functions provided by Windows. This requires the use of specific C data structures quite often and is therefore more comfortable to program in C++.
Download PyBox
Here are the necessary files for detailed information and installation:
- Readme file (text file)
- Installation instructions (text file)
- Windows installer (exe file, installs Python 2.7 in case it doesn’t exist)
Read about PyBox
The main reference on PyBox is the Diploma Thesis of Christian Schönbein. There is also a 11-page paper published at SICHERHEIT 2012 for those who want to have a more academic reference for citations.
- Christian Schönbein: PyBox – A Python Sandbox. Diploma Thesis, University of Mannheim, May 2011. (pdf file)
- Markus Engelberth, Jan Göbel, Christian Schönbein, Felix C. Freiling: PyBox – A Python Sandbox. Proceedings of Sicherheit – Schutz und Zuverlässigkeit (SICHERHEIT), Gesellschaft für Informatik, Darmstadt, March 2012.
Let us know
If you are using or have used PyBox in a research project, we would be interested to know.