AppTAN (In)Security: (In)Security of App-based TAN Methods in Online Banking
(In)Security of App-based TAN Methods in Online Banking
Authors: Vincent Haupert and Tilo Müller, System Security and Software Protection Group.
Abstract: German banks are increasingly turning away from the established TAN methods. Their incentives for developing new technologies to replace the indexed TAN list, mTAN and chipTAN are both improved security and usability, which cannot be met with dedicated hardware. New app-based methods allow the user to initiate a transaction with his mobile device (Android or iOS), and to confirm it on the same device, with supposedly more security than in the established methods. We have evaluated the security of such app-based methods using the pushTAN method of the Sparkassen-Finanzgruppe savings banks as an example, and we can certify that the method has serious conceptual weaknesses. The deliberate decision not to use independent hardware for the transaction initiation and confirmation makes the method an easy prey for malware. To demonstrate these weaknesses, we developed an attack that captures transactions from the user and manipulates them at whim before their confirmation.
Press release FAU: An easy target for hackers (English) / Leichtes Spiel für Hacker (German)
Written report: (In)Security of App-based TAN Methods in Online Banking (English) / Auf dem Weg verTAN: Über die Sicherheit App-basierter TAN-Verfahren (German, GI SICHERHEIT 2016)
Demo: Version 1.0.4 (German, Oct 2015), Version 1.0.7 (German, Dec 2015)
Talk: 32. Chaos Communication Congress (German, Video, Slides)
Screenshots:
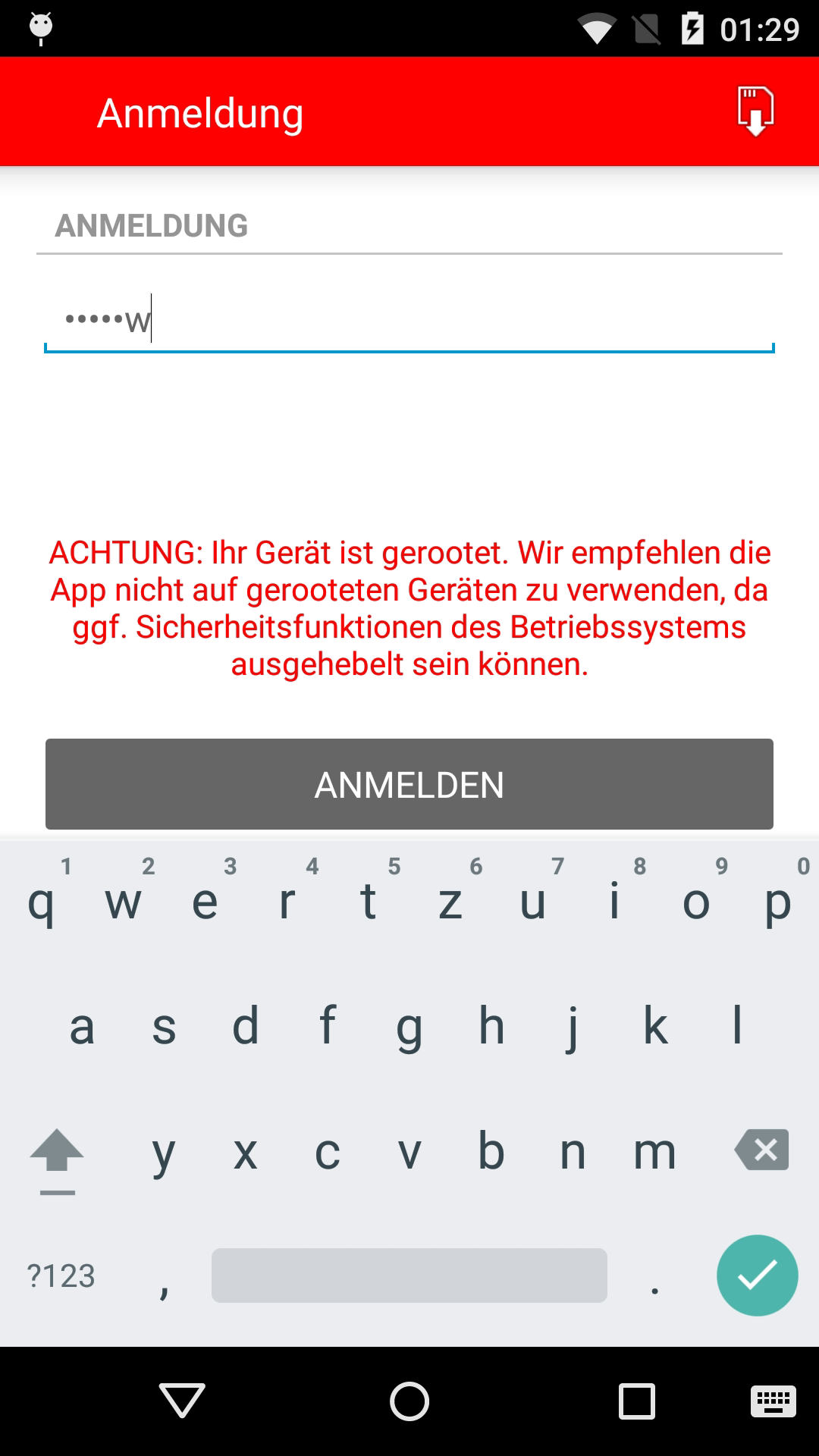
1. |
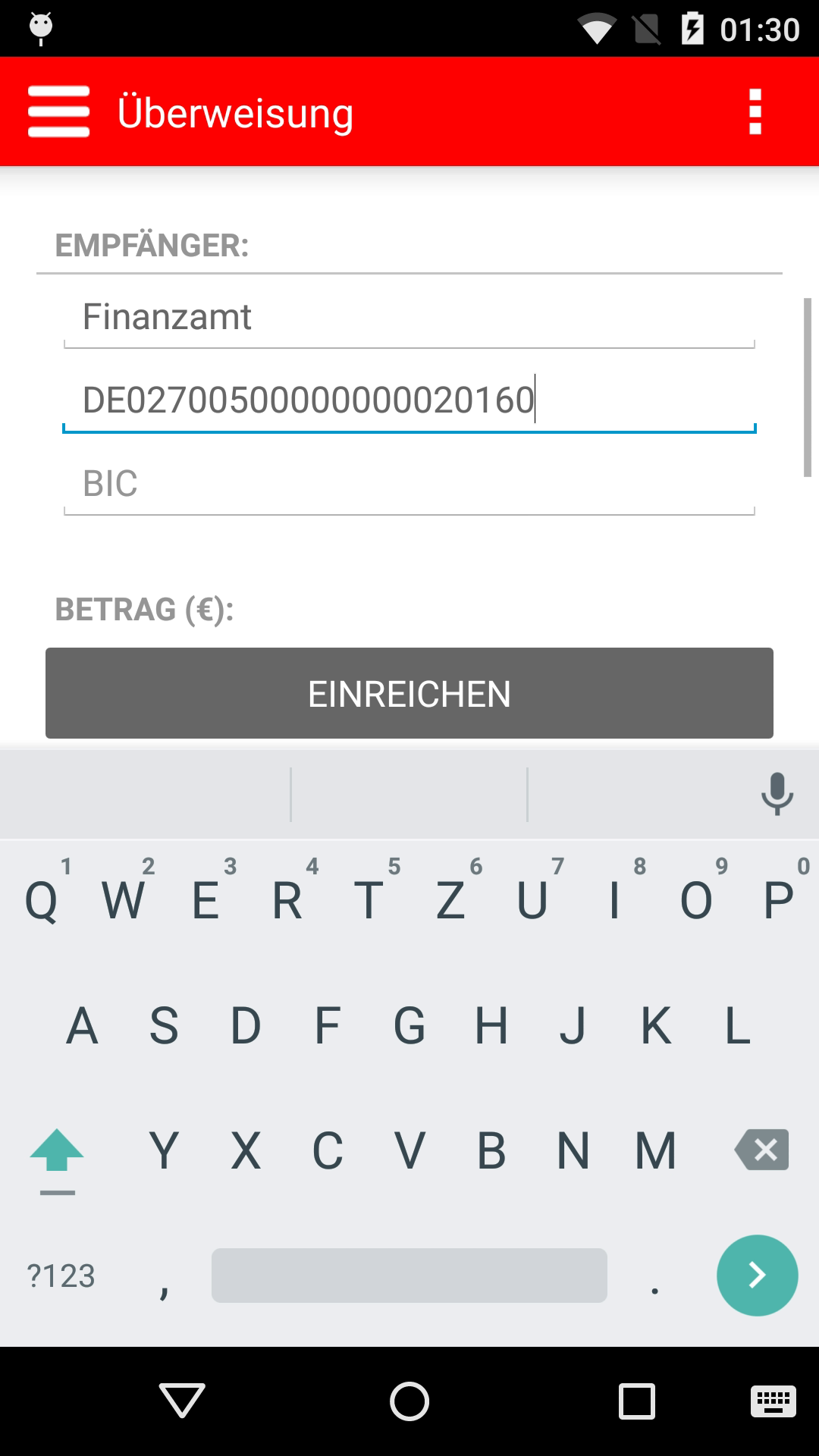
2. |
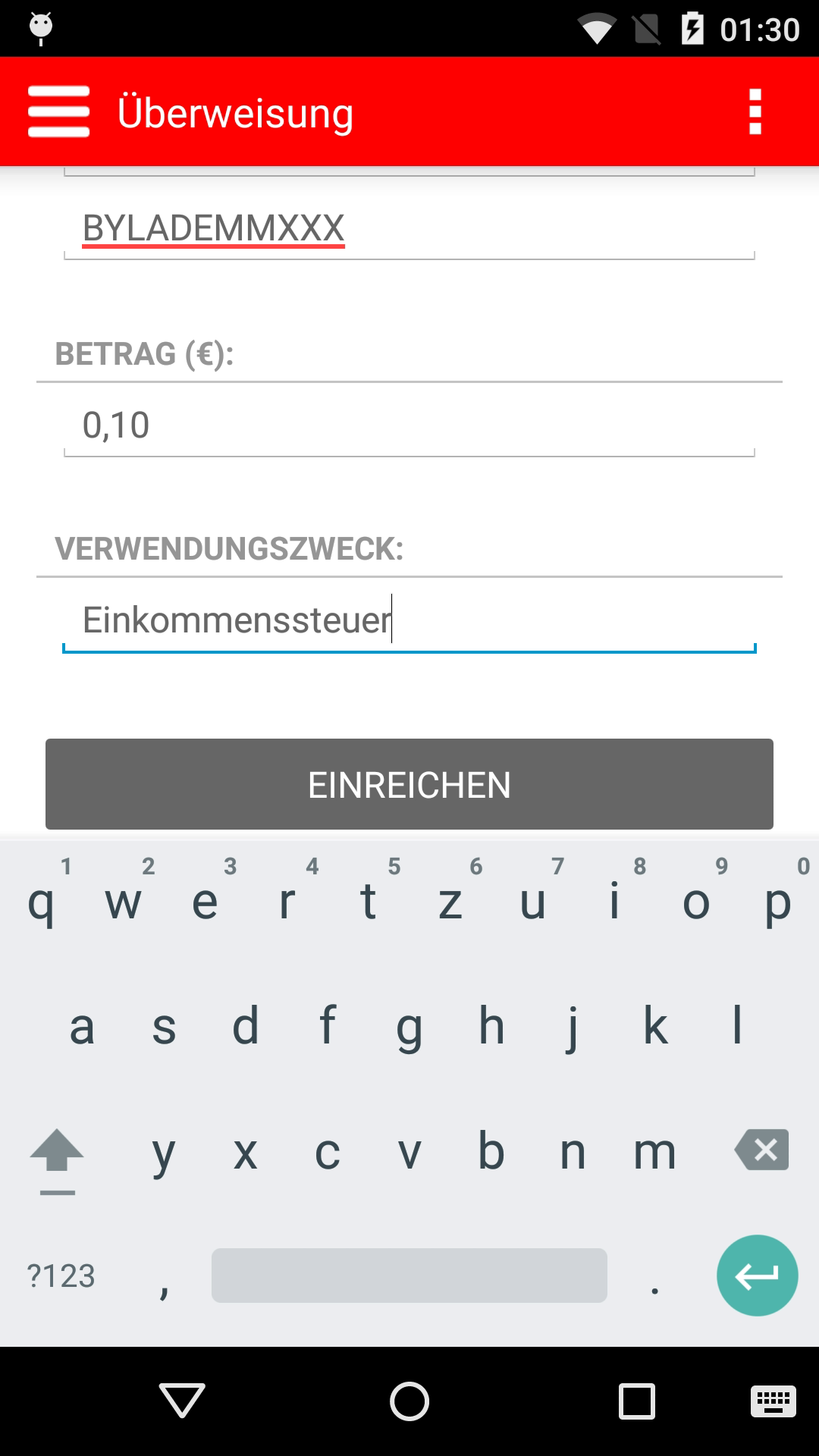
3. |
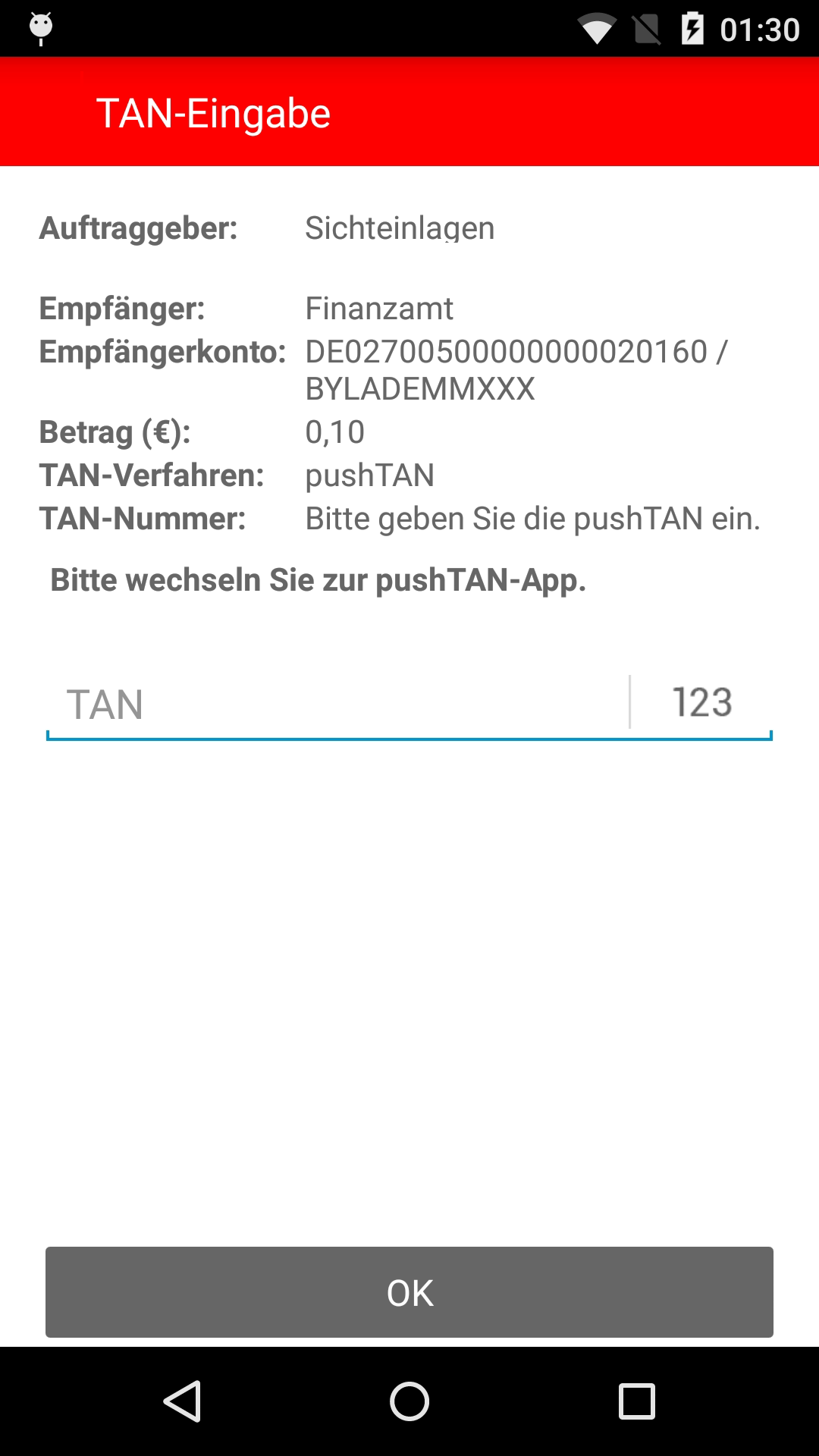
4. |
5. |
6. |
7. |
8. |
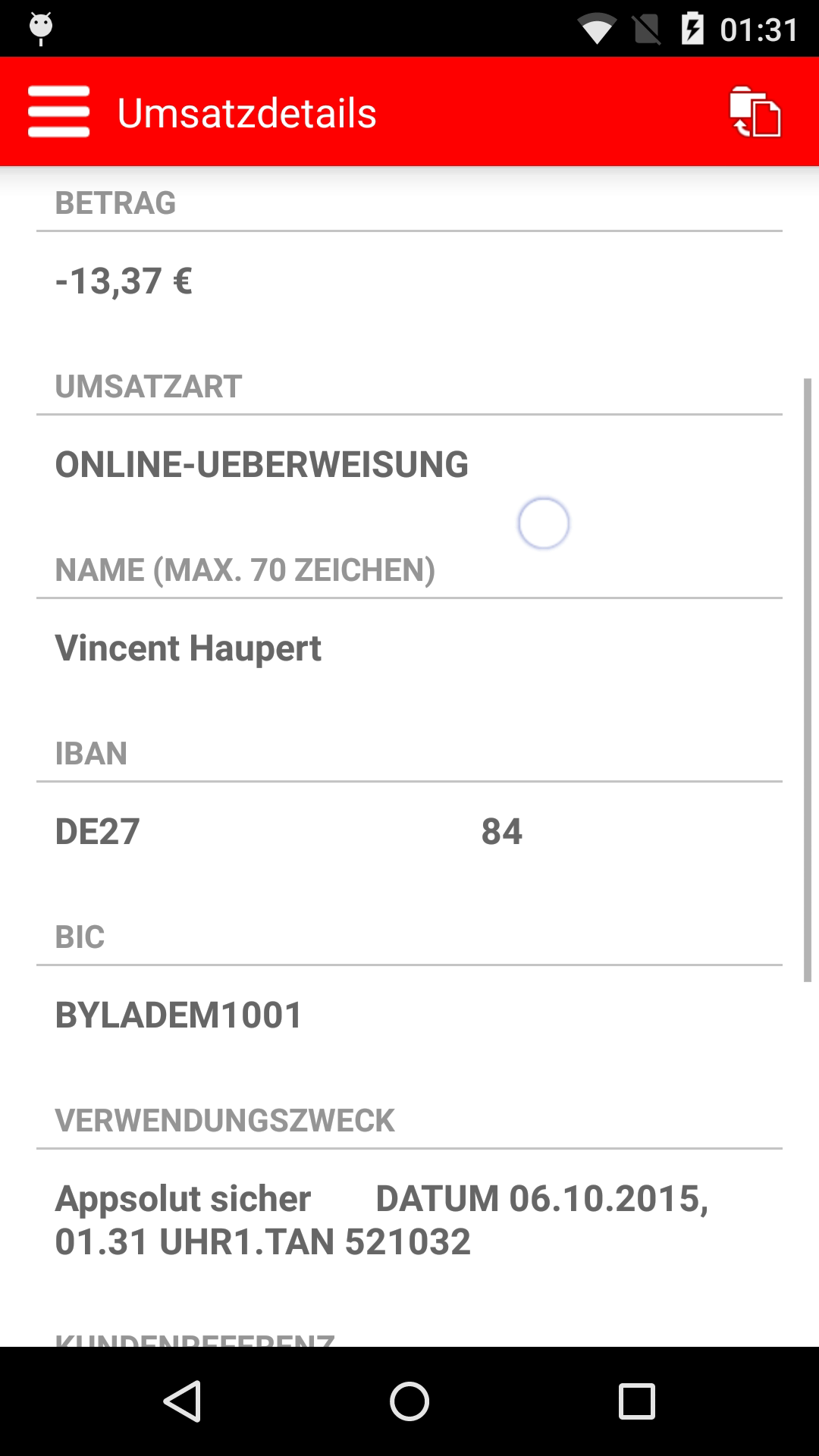
9. |
Please note:
- Implementation details have been blacked out and are independent of the conceptual weaknesses of app-based methods. The pushTAN method of Sparkasse serves explicitly as a possible example of our analysis. The security deficits of the Sparkasse app, as compared to other financial institutions that use similar methods, is out of scope.
- To avert damage to third parties we publish no programs, no code and no technical details which go beyond our written report—also not upon request.
 All content of this website is licensed under a Creative Commons Attribution-NoDerivatives 4.0 International Germany License.
All content of this website is licensed under a Creative Commons Attribution-NoDerivatives 4.0 International Germany License.